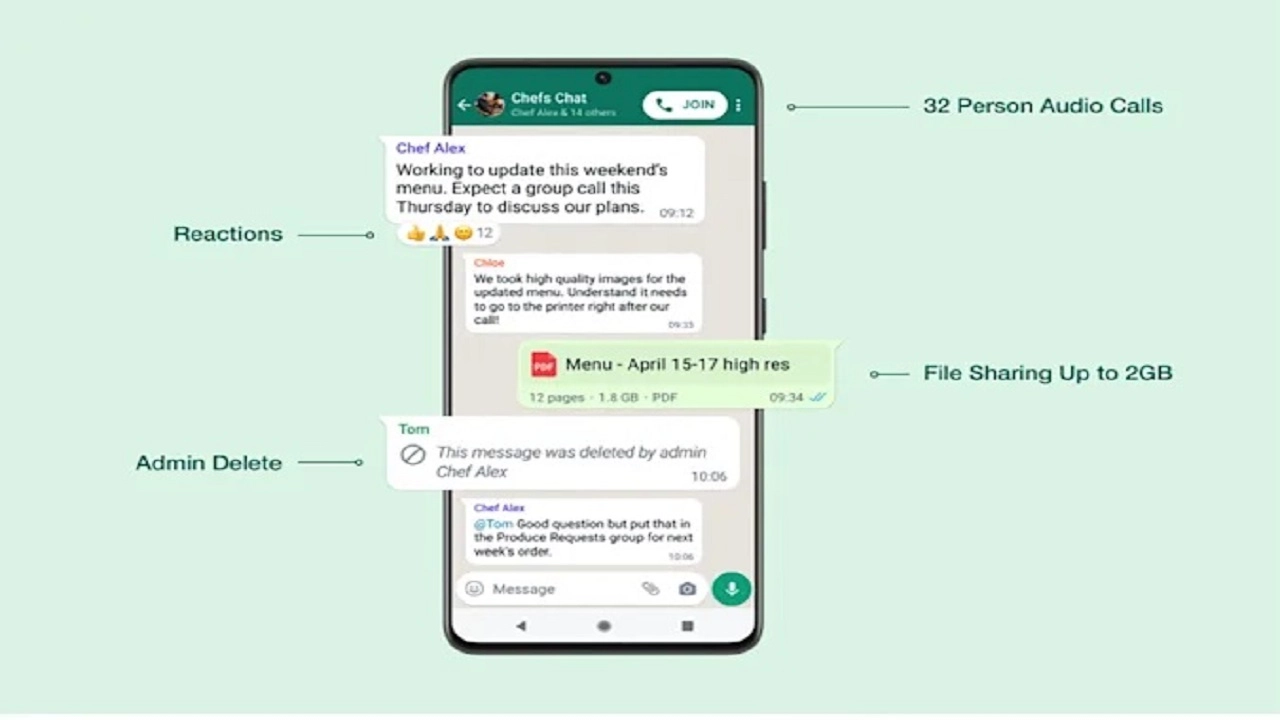
WhatsApp is one of the most popular messengers in the world, but it is functionally inferior to the competition in many respects. However, this is slowly changing and he is gaining more and more opportunities.
Author: Sachin Mahto
How to create a strong password when cyber attacks are getting louder? Take care of your access!
How do I create a strong password? Who needs this and why such a question? The situation in the east very quickly raised the topic of cybersecurity and online threats. Fear was a natural consequence, on the one hand, of the very fact of starting a war in a neighboring country, and on the other hand, of a wave of threats about cyberwar, unlike anything the world had ever seen before.
SBC, AAC, AptX, LDAC – which Bluetooth codec is the best and why?
Bluetooth codec are an integral part of any audio device with Bluetooth connectivity. There are a lot of them to choose from , for example: SBC, AAC, AptX, AptX LL, AptX HD, AptX Adaptive, LDAC and HWA. Each of them has its own application, but not every device will handle all of them.
Editing Twitter posts? Elon Musk is planning a new cleanup
Elon Musk has barely become Twitter’s largest shareholder and is already planning to make changes. Well, he posted a survey on the site in which he asks users if they want an edit button. Yse and on can be selected as answers . This is a fairly clear suggestion that the main aim is to correct minor errors such as typos.
How to protect yourself from online threats? Spoofing, phishing and other cyber attacks
The Internet has never been a completely secure medium. Criminals are using increasingly sophisticated tools to extort data and money. The times when the Nigerian scam was the pinnacle of finesse are long gone. We explain what spoofing, phishing, smishing and other cyber attacks are and advise on how to avoid them.
Installation of Windows 11 without TPM and supported processor. How to bypass security?
The latest version of Microsoft’s operating system has surprising hardware requirements. If you are wondering if there is a hidden wicket and it is possible to install Windows 11 without TPM and supported CPU, we have good news. We explain how to bypass security.
How do I block a number? Spam, photovoltaics and other vending machines
Telephone spam is unfortunately something we encounter every day. Phishing and the inflated costs of intermediation in programs for co-financing photovoltaic panels, long ago took the proportions of the Egyptian plague. Are you wondering how to block a number and fight the call machines? Introducing applications for blocking bots and telemarketers.
One of the best VPNs now over 80% cheaper, plus 2 months for free – it’s a pity not to use it
A good VPN can be a huge expense, so any savings are worth its weight in gold here. Surfshark , one of the best VPNs on the market, is now available with over 80% off a 2-year subscription, plus you get 2 months for free.