The Internet has never been a completely secure medium. Criminals are using increasingly sophisticated tools to extort data and money. The times when the Nigerian scam was the pinnacle of finesse are long gone. We explain what spoofing, phishing, smishing and other cyber attacks are and advise on how to avoid them.
Contents
Online threats. The rise of cybercrime

We live in times when it seems impossible to function without internet access. The Internet makes life easier on practically every level of everyday existence, and cybercriminals are well aware of it .
Regardless of whether the network is a source of knowledge for us, allows us to work, study or pay bills without queuing at the post office, we leave a digital footprint and sooner or later we will become a target.
Anything can be an attack vector . After all, we connect to the network constantly and each of us has a telephone number and email address . There is no person who will never receive a suspicious text message, e.g. from a courier or energy supplier, and well-written phishing emails will not always end up in spam.
The forecasts of Cybersecurity Ventures analysts reveal a disturbing picture of the true boom in cybercrime . Over the next five years, its profits will be five times higher than global international crimes , such as drug, human and arms trafficking, oil theft, and illegal mining and fishing. According to the FBI 2021 Internet Crime Report , criminals earned nearly $ 7 billion in this way last year.
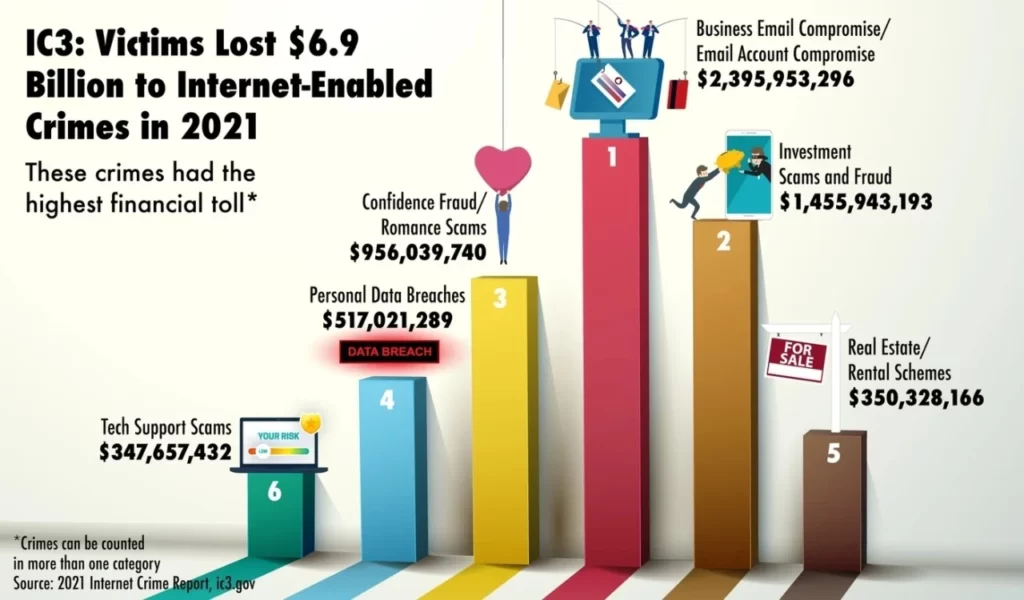
What is the situation in our home yard ? The data included in the police statistics show that in 2020 in total almost 55,000 crimes related to cybersecurity were recorded . This is an increase by more than half compared to the 2018 report.
Spoofing. When someone is impersonating a trustworthy number
The greatest threat is posed by forms of cyber attacks that are not yet well known to us. These include, for example, CLI (Caller ID) spoofing and the use of ransomware .
In the first case, the offender uses a known number that does not raise our doubts. On the phone screen, we can see a call from a bank or service provider , for example . How it’s possible? This mechanism was described in January by the a website:
“To set up such a conversation, all you need to do is use one of the many online services. We will not give their names here, but each of them allows you to enter the number of the person you want to call and the number you want to introduce yourself for a small fee. And then you press the “call” button and that’s it.

Unfortunately, not all operators verify whether the calling subscriber uses the assigned number. This state of affairs is also caused by outdated protocols in mobile networks that were not developed with the intention of accurately authenticating callers .
Read Also: How do I block a number? Spam, photovoltaics and other vending machines
This attack is especially dangerous in a situation where the calling scammer also knows our basic data (e.g. from one of the previous leaks from online stores). This will allow him to make the conversation more credible and easier to navigate the rules of social engineering to gain an advantage. First, we will see the correct bank number, then we will hear your name and surname and a request for verification of our person (standard procedure when talking to a financial institution).
At this point, we will be asked for information that the criminal does not have yet , and later, depending on the conversation scenario, it will be required to install the application or provide further data, e.g. a payment card.
Ransomware, that is, hijacking our data and making ransom demands
Most ransomware attacks start with an email that contains a harmless-looking link or attachment (such as an office suite document). It is enough to open a redirect or a file to unknowingly run encryption of the hard disk content in the background (network drives are also at risk!).
Encryption is most often performed using the Advanced Encryption Standard (AES) with a 128 or 256-bit key, thanks to which intruders can be sure that we will not be able to recover the data. After completing the operation, we can unblock access in one way – by paying with cryptocurrency for the decryption key .
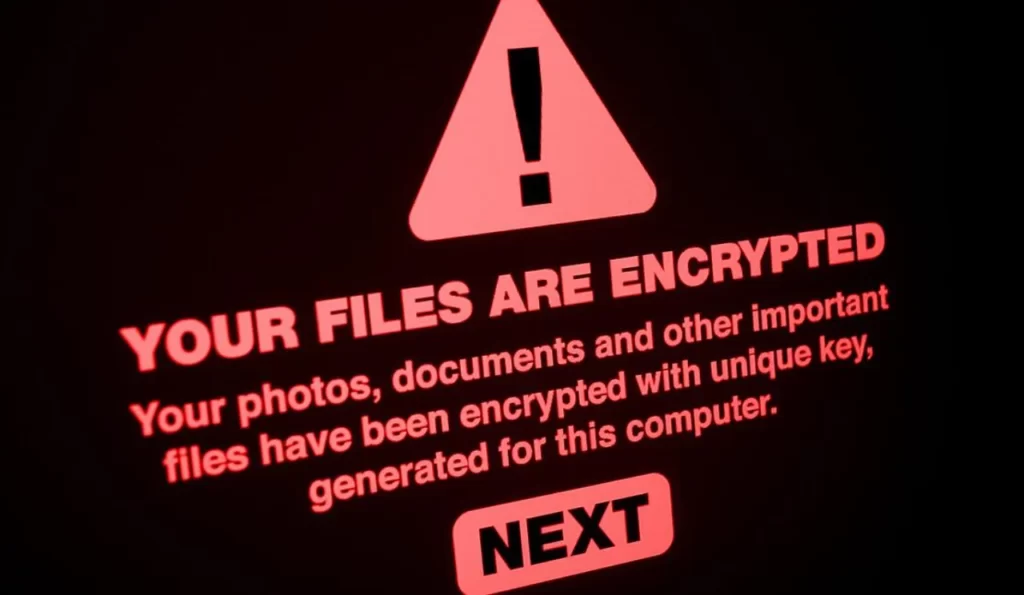
If the software has infected a private person’s computer, data loss may not be so painful, but imagine what happens to a company whose IT department has not taken care of regular backups .
Phishing and Smishing. Phishing of data by e-mail and SMS
If I had actually accumulated all the funds allegedly won or received in confidence by email, I would be in the Bahamas at the moment. The various iterations of the Nigerian scam , the form of which has evolved over the years, ultimately boil down to one thing – phishing in various forms. Ultimately, if we are to get something for free, we must provide our details and bank account number, and the appetite of criminals will grow as we eat.

Sometimes phishing is masked a bit more intelligently, simulating communication with a bank, service provider or private person known to us. The scenarios after clicking on the link or our answer are various – we can even land on a professionally prepared page that is a copy of the original site.
Another form of phishing, the so-called smishing . In this variant , SMS text messages are used, which pretend to be, inter alia, courier companies (“parcel surcharge required”), electricity or gas suppliers, contractors who have problems with our invoice or classifieds websites, such as OLX or Allegro. Criminals also react to the calendar of events , such as the Great Orchestra of Christmas Charity or important sports events.
If, after clicking on such a link, we provide correct data on a crafted payment page, we can expect the account to be cleared.
Scam on WhatsApp, i.e. I bought your item on OLX
The scam on WhatsApp , notoriously reported in our country , deserves a separate mention . This is obviously a form of phishing, and users of the OLX classifieds website are the victims .
The modus operandi in this case is very simple. After adding an offer to sell an item, we receive a message from someone keenly interested in the purchase. After the first messages, a request is sent for an e-mail or a link that is supposed to allow us to receive the payment . In fact, cyber criminals use this to extort confidential payment card details.
Broken People is a common feature of these messages , and sometimes the Cyrillic alphabet appears here and there (especially if we look at the intentions of our interlocutor).
False advertising of banking services in the Google search engine
Google search ads are not always safe. In short targeted attacks, fake ads pretending to be banks and financial institutions appear over the search results . In this way they were attacked, among others clients of BOŚ and BGŻ BNP Paribas banks.
Read Also: Great cleanup in Google Maps – this is how the company fights against fraud
Fraudsters prepare twin-looking pages in domains with a name that is confusingly similar to the original (e.g. one or two letters are replaced). People who do not exercise due caution click on the above-placed advertisement instead of the search result of their bank, enter their data and say goodbye to their funds.
Detecting this type of activity is relatively quick, which is why the fraudsters do not decide on long campaigns.
How to protect yourself against frauds and cyber attacks?
There is no ‘one- size-fits-all’ recipe as cyberattacking and phishing tools and phishing tools are constantly changing.
Universal advice is to use common sense and develop habits that will help us avoid problematic situations:
- we do not click on links or attachments from an unknown sender , regardless of whether they appear in an e-mail, instant messaging or text message,
- pay attention to whether the content of the message matches the sender we know, and if we are not sure, call him (a friend on Messenger who suddenly sends a chain of happiness with a link? maybe someone has just lost access to the account),
- do not provide sensitive data and resist social engineering – only scammers will ask for a login or password, ask for the installation of the application or for the full card number, expiry date or CVV2 / CVC2 code,
- let’s use the simple principle of limited trust when answering phone calls – we can always hang up and call the service provider or bank ourselves.
Read Also: Site infected form viruses – what to do?

