Among the many available ways to strengthen your online security, two-factor authentication can be classified as one of the most important. By using such a security, we will significantly hinder the activities of cybercriminals who would like to break into our account. If you’ve heard somewhere about two-factor authentication, but don’t know exactly what it is or how to set it up, this guide is for you.
Contents
What is two-factor authentication and how does it work?
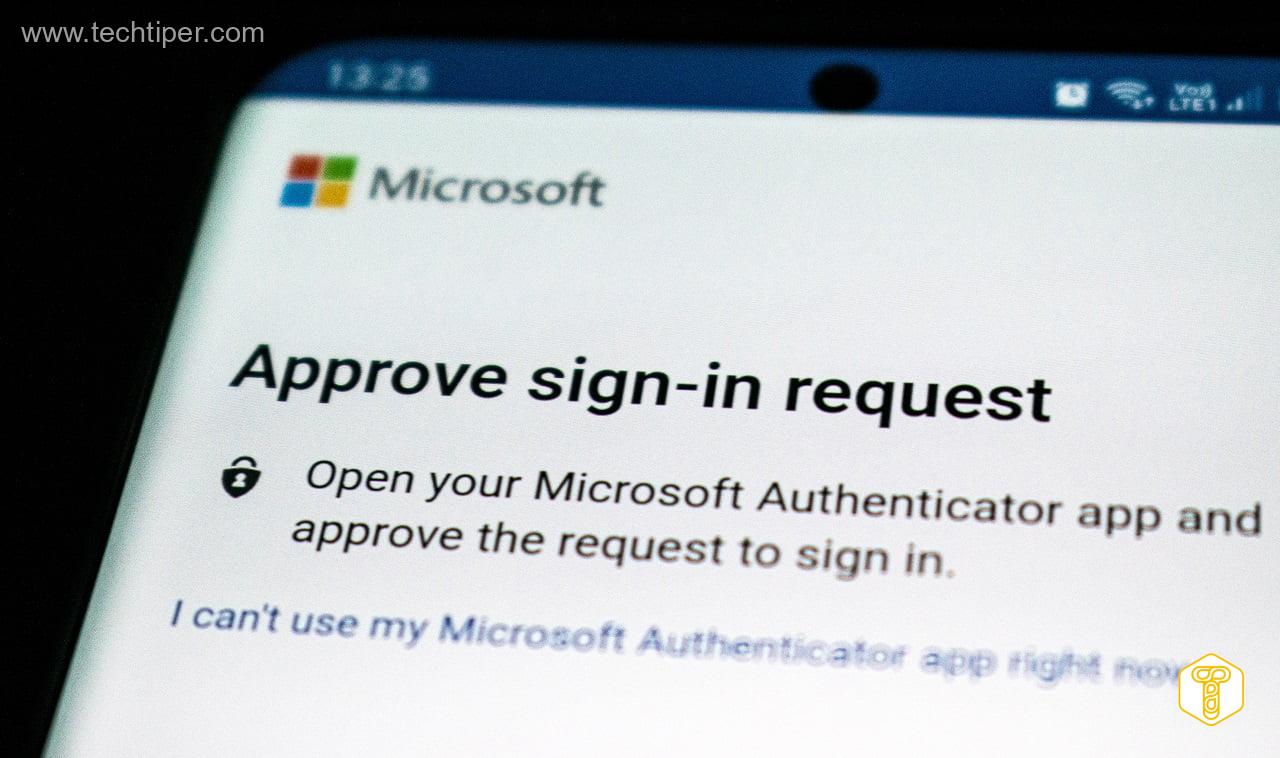
Two-factor authentication (2FA) is a tool to verify that the person trying to access a given resource is really who they say they are . Let’s explain it using an account on a social network as an example. Usually, you only need to enter your e-mail address or username and password to log in to your profile.
If we set up two-factor authentication, the login procedure will be longer. After entering the correct data, the system will ask us to enter the previously selected second component , e.g. a code received in an SMS. Only after passing this stage will we gain access to our account.
Different companies and service providers on the network may have different two-factor authentication methods . Special codes can be generated in the application of a given entity or in a separate application. There are also separate devices from which we can confirm who we are. However, the most frequently used codes are sent to our telephone number via SMS.
Depending on the provider of two-factor authentication and the settings you choose, this method may not be required every time you sign in . Sometimes we will only be asked to enter the second component when trying to log in from a new device or when trying to perform major operations on the account.
Two-factor authentication – advantages and disadvantages

In fact, the only significant downside to two-factor authentication is the time you spend setting up and logging in with it. Reaching for the phone and rewriting the code received via SMS will take us longer than just entering the e-mail address and password.
You should also remember to have a login device with you . For example, we may have a problem when our smartphone is discharged or we just don’t have it with us, and we want to access our account. The solution may be one-time codes previously received on a given website – such a method is provided by, for example, Google.
Experts have no doubts that it is worth using two-factor authentication. This is one of the most important components in the world that ensures a higher level of security for the end user, especially for the one who is unable to implement other mechanisms – tells us Dawid Bałut, security director at Egnyte.
When we have such authentication, and the cybercriminal has set up a fake website, e.g. Facebook, to intercept login and password, he will not be able to effectively take control of our account – he explains.
Thus, two-factor authentication protects us when cybercriminals come into possession of our e-mail address and password . Even when they try to use this data to log into our account, they will have to provide, for example, an SMS code that will come to our phone. Thus, their operation will fail.
Read Also: How to create a strong password when cyber attacks are getting louder? Take care of your access!
How to set up two-factor authentication?
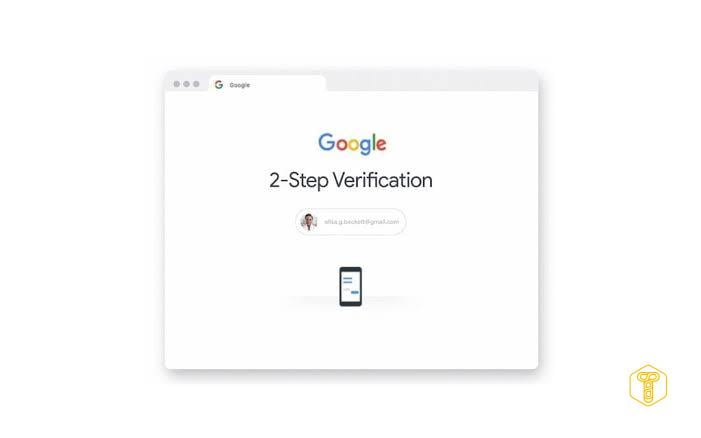
If we have such an opportunity, we should configure two-factor authentication , at least for the most important accounts for us, the taking over by cybercriminals would have very negative consequences. Below are some examples of how to set this method for popular platforms.
- Facebook : go to settings and privacy> settings> security and login> two-factor authentication. On the page displayed, we can choose which method we want to use. It can be a code in an SMS message, a code in an authenticator application, a security key and a code to regain access.
- Twitter : we select the option more and settings and privacy . Then click on security and account access> security> two-step login verification. We can choose between an SMS, an authentication application and a security key.
- Google : go to the website of the Google security center and select the option enable two-step verification . Then choose Google login: two-step verification . On the page displayed, we can check whether we already use two-factor authentication and configure individual methods of confirming identity (confirmation in the form of notifications on the phone, SMS, voice call, backup codes, Authenticator application, security key).
Two-factor authentication is one of the most important, but not the only, element that allows you to ensure security on the network . For more tips, see our guide on how to start building your cybersecurity .

